This blogpost is also posted on the PepperCrew website.
There are a lot of different certificate file formats that can be involved in a SSL certificate implementation as explained in my previous blogpost. This blogpost focused on the different methods to create and import these files onto the Citrix NetScaler and showing you how to assign the right SSL certificate to your virtual server for load balancing or gateway services. You can read all about the different certificate (and certificate archives) file formats in my previous post.
With all the instructions included in this blogpost it has become a rather long post, so I’ve added a small index to quickly navigate to the different sections:
– Creating a private key on the NetScaler
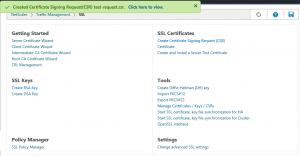
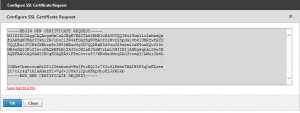
– Creating the certificate signing request on the NetScaler
– Creating the certificate signing request with Internet Information Service
– Importing a PKCS#12 (.pfx file format) certificate store on the NetScaler
– Importing a PEM certificate store on the NetScaler
– Importing the root and/or intermediate certificates on the NetScaler
– Creating the certificate chain on the NetScaler
– Binding the SSL certificate to a virtual server on the NetScaler
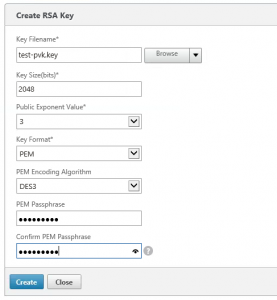
Creating a private key on the NetScaler
As pointed out correctly by Barry Schiffer in my previous post, working with SSL certificates on the NetScaler starts with the creation of the private key.
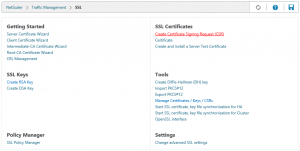
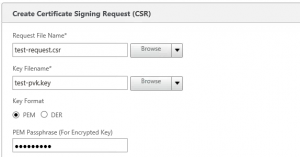
Creating the certificate signing request on the NetScaler
When a private key is created, you can continue to create a Certificate Signing Request on the NetScaler.
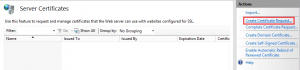
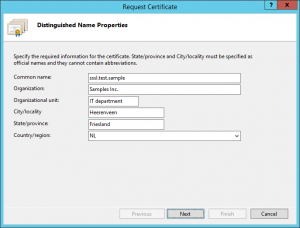
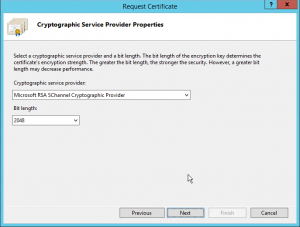
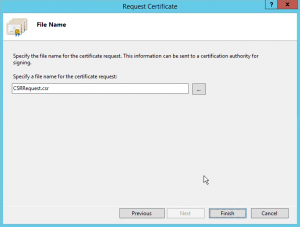
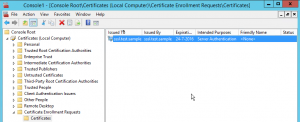
Creating the certificate signing request with Internet Information Service
As some prefer to use the Internet Information Service console to generate the Certificate Signing Request (which automatically generates a private key), I have included the instructions in this blogpost as well
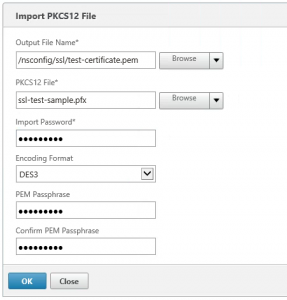
Importing a PKCS#12 (.pfx file format) certificate store on the NetScaler
If all goes well, you will receive your certificate in a PKCS#12 (certificate store) format from your Certificate Authority after you requested your certificate and provided them with the CSR. Even though Citrix offers a great support article (CTX136444) on the import of PKCS#12 file into the NetScaler, I did include the instructions in this blogpost to offer a complete reference. The NetScaler works best with PEM (Base64-encoded) certificate and needs to convert a PKCS#12 certificate store into a PEM certificate store format.
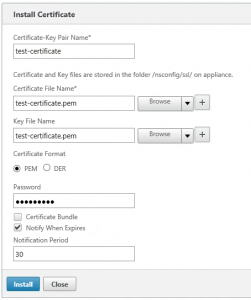
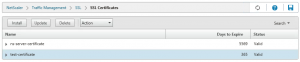
Importing a PEM certificate store on the NetScaler
If a PEM (Base64-encoded) file is provided, the previous import step is not required and the certificate can be imported right away on the NetScaler using a different wizard.
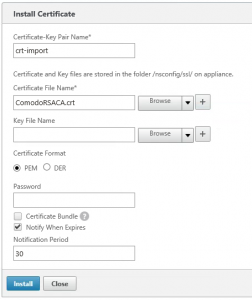
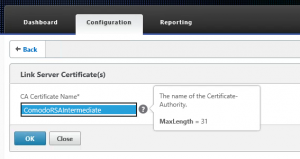
Importing the root and/or intermediate certificates on the NetScaler
Root and intermediate certificates can usually be downloaded from the Certificate Authority as a single certificate PEM or DER encoded file. These files are usually not password protected.
You can import the intermediate and root CA certificates with the following steps:
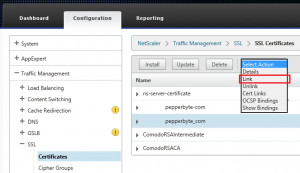
Creating the certificate chain on the NetScaler
To ensure no SSL Error 61 messages are shown when a user connects to a XenApp or XenDesktop site through the NetScaler, you will need to make sure that all certificates in the certificate chain (or certificate path) are available on the NetScaler and are linked correctly. To create a certificate path on the NetScaler you need to link the server certificate to the Intermediate CA certificate that issued it and the Intermediate CA certificate to the Root CA certificate that issued it. So each certificate needs to be linked to the Certificate Authority that issued the certificate to create the entire certificate chain from server certificate to root CA (and all Intermediate certificates in between). Here are the steps to link certificates on the NetScaler to create the certificate chain:
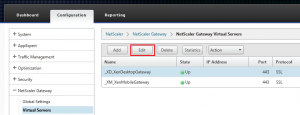
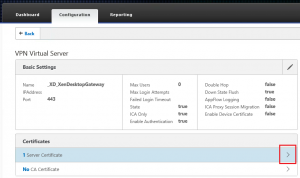
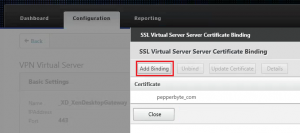
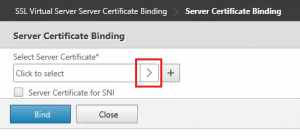
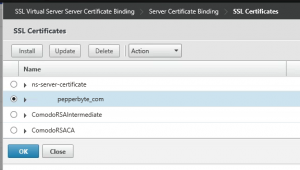
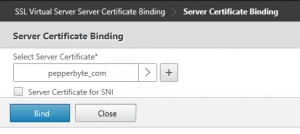
Binding the SSL certificate to a virtual server on the NetScaler
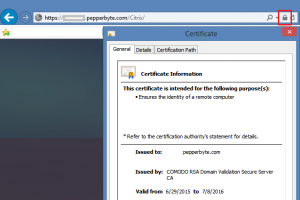
After all the required actions are done to request the certificate, import the server, intermediate and root certificates and link them together to create the certificate chain we can finally assign (or bind) the certificate to the Virtual Server on the NetScaler.
As the NetScaler has different Virtual Server types, I’ve used a Gateway Virtual Server as an example. Even when a certificate is already assigned to the Virtual Server, the steps to perform will be the same.
The following sources have been used to create this post:
How to Generate and Install a Public SSL Certificate on a NetScaler Appliance
Digicert: IIS SSL Certificates Creation
How to Convert PFX Certificate to PEM Format with the NetScaler Wizard
How to Install an Intermediate Certificate on Access Gateway Enterprise Edition Appliance
Hi Esther. Thanks for another encryption post. I like ’em.
Tidbits:
You wrote:
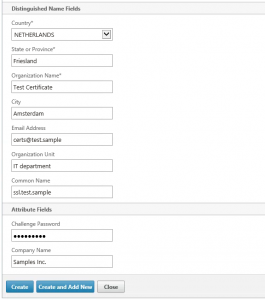
Also note down the chosen challenge password as you will need to provide this password later on.
No. Don’t. In fact leave the “challenge password” field empty. (And then update the screenshot at https://www.virtues.it/wpitq/wp-content/uploads/2015/07/SSLCertsOnNS09.png) Whatever you type in there will end up in clear text in the CSR. And you may not want this. What you type in there is not used for encryption of any kind.
Nobody really understands this feature, but the idea was that you could communicate arrange a secret password with your certification authority. And if you should ever want to revoke your certificate, then they would ask you that “challenge password”. — But: No CA actually does this.
Further details:
https://security.stackexchange.com/questions/77028/whats-the-use-of-challenge-password-in-build-key-server-and-build-key-from-easy
Cheers from Germany,
Hendrik
Hi Hendrik,
Thanks once again for sharing your knowledge on the subject. Another learning experience for me as well 🙂
I’ll update the post and add your explanation to it for sure, I love to get my facts straight 🙂
Cheers,
Esther